
The EU's Digital Operational Resilience Act (DORA) came into force on 16 January 2023 aiming to harmonise cybersecurity, mitigate risks, and increase the digital operational resilience standards across the financial sector within the EU.
In this article Ocorian's DORA specialists Sharon Hodder, Stuart Geddes, Jehan Dossin, Ben Arram and Niamh Blake answer FAQs on everything from staff training to ICT frameworks so that management teams can get ahead of the looming implementation deadline of 17 January 2025.
1. Who is responsible for compliance with DORA?
The responsibility for compliance with DORA lies with the management body of the in-scope regulated financial entity. Under DORA, this body holds ultimate accountability for the entity's information and communication technology (ICT) risk management and operational resilience strategy. The regulatory expectation is that the management body will closely oversee digital operational resilience-related risks, ensuring compliance with DORA’s varied and detailed technical and policy obligations at a minimum.
In practice, the management body is the Board of Directors (the Board) who effectively run the entity or have key functions in accordance with relevant union or national law. Entity Boards should ensure they have sufficient oversight of, input into, and control over ICT policies and procedures to discharge their obligations under DORA.
2. What responsibility does the management body have?
DORA places a regulatory obligation on the Board to “define, approve, oversee and be responsible for the implementation of all arrangements related to the ICT risk management framework”. This involves:
- Setting your firm's overarching DORA strategy
- Putting appropriate data security policies in place
- Establishing appropriate governance arrangements for ICT functions, with clearly defined roles and responsibilities
- Overseeing the implementation of suitable ICT business continuity and disaster recovery arrangements, including regular reviews and approval of these arrangements
- Reviewing and approving your firm’s ICT audit arrangements
- Ensuring appropriate financial and non-financial resources are available to meet your firm’s DORA needs
- Ensuring sufficient DORA and ICT security training is provided to and undertaken by all relevant staff (including the Board)
- Regularly reviewing and approving your firm’s ICT outsourcing arrangements
- Putting suitable reporting channels in place to enable timely notifications to the Board of changes to any ICT outsourcing arrangements and the potential impacts of those changes
Whilst thee accountability for these regulatory obligations cannot be delegated, in practice the Board will assign many of these tasks to appropriately skilled, knowledgeable and experience specialists within their organisation.
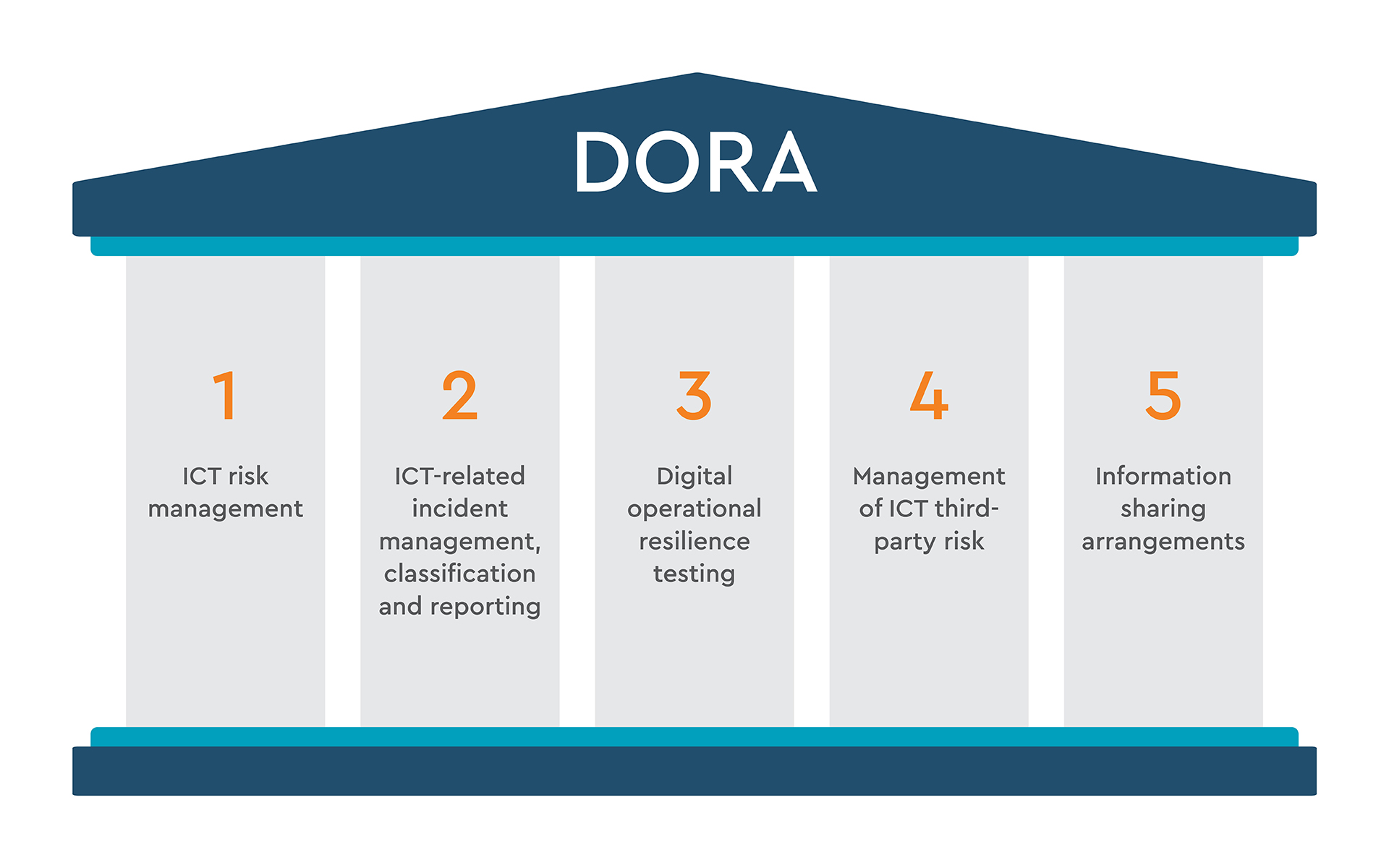
3. What appointments arising from DORA need to be made by the management body?
When it comes to ICT risk management, local regulators have made it clear that sufficient knowledge and skills in ICT risks will be considered as part of the suitability requirements for Board members of financial entities. This requirement will apply to current and prospective Board members. While every Board member should ensure familiarity with ICT risks to support the Board in the discharge of their obligations, in scope entities should consider appointing at least one member of the Board or senior management as a DORA Responsible Officer who will oversee the firm’s DORA compliance.
This role will be viewed as part of the second line control function and the Board should ensure an appropriate level of independence. Subject to the scale, nature and complexity of your firm’s operations and business activities, this role may be assigned to someone already serving as Chief Risk Officer or Compliance Officer, where local regulations and time commitments allow.
Members of the Board should be cognizant of the fact that they cannot delegate responsibility for their regulatory obligations under DORA to any one individual, to a Group resource or to a third party. It is, therefore, crucial that all members of the Board engage fully with all DORA projects and workstreams in order to discharge their obligations under the regulation – this means having ICT risk management as a regular agenda item in Board meetings, not just a passing mention.
4. Who else should be included in DORA preparations?
We recommend creating a RACI matrix, a project management tool that stands for Responsible, Accountable, Consulted, and Informed. This will help define who is responsible for doing what, who is ultimately accountable, who needs to be consulted, and who should be informed.
Remember, while responsibilities can be delegated, accountability rests with the Board. So, it is crucial to have clear roles and responsibilities for all ICT risk-related functions.
Lastly, conduct a gap analysis of your existing digital operational resilience arrangements against your firm's DORA requirements. This will help you understand where you stand and what needs to be addressed.
If you haven't started this process yet, it's important to do so quickly (and you may wish to seek specialist external support to help you), as it can take months to complete.
5. How should the management body think about ICT risk management?
The first step is to ensure that your business strategy is aligned with your digital operational resilience strategy. This alignment is crucial and a good opportunity to review and refresh your strategic objectives if you have not done so recently. It's not about retrofitting solutions; it is about integrating resilience into the core of the business strategy from the outset.
ICT Risk management involves identifying the critical services that your business provides to your clients, and the important functions needed to deliver these services and continue operating as a regulated financial entity. Once these services are identified, the next step is to ensure that the systems supporting these services—often referred to as ICT assets—are resilient.
The goal is to minimise or prevent any interruption of service to clients. For example, if a fund accounting services application were to fail, the business must have a plan in place to continue providing these services.
To achieve this, your business must not only take preventative measures to reduce the risk of an operational or security incident from occurring, you also need to have backups in place and ensure high availability of your ICT systems. Ideally, there should be a replacement system ready to switch over within a specified period. While having duplicate systems for everything might seem extreme, it is a standard covered by regulatory requirements. The Board is responsible for ensuring that these measures are in place behind the scenes.
In practical terms, this means having regular backups and ensuring that third-party service providers also have robust and effective backup and recovery plans. For instance, if a third-party SaaS (Software As A Service) systems were to fail, your business would rely on the service provider, to have backup centres and secure copies of all data.
For systems hosted internally, high availability solutions should be implemented so that, if one server goes down, another can take over seamlessly. The goal is to have the capability to restore your services in a timeframe aligned to your business needs and broader regulatory obligations (such as mandated Recovery Time Objectives). This ensures that the business can continue to provide critical services to its clients even in the face of significant disruptions.
6. How should the management team build a comprehensive ICT risk management framework?
We recommend putting the following in place:
Business continuity plans:
- Regular review and updates of plans to address evolving threats and industry-specific risks.
- Emphasis on documentation and clear communication of plans to all relevant stakeholders.
- Ensure you test your plans at least annually or following a critical incident or material changes to your ICT infrastructure.
Cyber security monitoring:
- Proactive monitoring of networks and systems for vulnerabilities and potential threats.
- Incident response procedures in place to address security breaches promptly. These should be rehearsed at least annually.
- Lessons learned from past incidents incorporated into future planning.
Risk assessment and mitigation:
- Identification and evaluation of potential risks to business operations.
- Implementation of appropriate mitigating controls to minimise the impact of risks.
- Regular review and update of risk assessments.
Third-party risk management:
- Assessment of risks associated with third-party suppliers and vendors and ensure you are capturing and reviewing risks associated with onward subcontracting
- Ensuring that suppliers adhere to the company's security standards.
Testing and training:
- Regular testing of business continuity plans to ensure their effectiveness.
- Ongoing training of employees to raise awareness of cyber security threats and best practices.
Scenario development:
- Developing well thought out severe yet plausible stress scenarios to be used when undertaking risk assessments and testing your continuity arrangements.
- Maintaining a range of appropriate systemic, idiosyncratic and combined scenarios that are relevant to your business, industry and operating environment.
- Considering suitable time horizons over which the scenarios run, taking into account factors such as micro and macro-economic cycles and seasonality
Governance and reporting:
- Clear governance structure in place to oversee business continuity and cyber security initiatives.
- Assigning roles, responsibilities and of risk ownership to appropriate individuals and maintaining clearly defined reporting lines.
- Regular reporting to the Board on the status of these initiatives.
7. What policies and procedures should management teams put in place?
DORA is prescriptive in relation to certain types of policies and procedures that you are required to maintain.
Local regulators will expect you to have in place documented policies, standards and procedures which address the identification, monitoring, mitigation, management and reporting of the firm’s ICT related risks. Local Boards should ensure approval, oversight and periodic review of the group policies and ensure that these are appropriately tailored from a regulatory and operational perspective for their business.
We recommend:
Documentation and review:
- Policies and procedures must be clearly documented and regularly reviewed to ensure they remain relevant and effective.
- Evidence of these reviews, such as Board minutes or audit reports, is essential for regulatory compliance.
Independent third-party assessment:
- Engaging independent third parties for audits and reviews can provide objective assurance of policy compliance.
- These assessments can identify areas for improvement and strengthen the overall governance framework.
Tailoring policies to local jurisdictions:
- While group policies can provide a foundation, they must be adapted to meet the specific requirements of local jurisdictions.
- This ensures compliance with local regulations and avoids potential risks.
Board oversight and approval:
- The Board plays a crucial role in overseeing the development, review, and approval of policies.
- Their involvement is not only a regulatory requirement, it demonstrates the Board’s commitment to governance and compliance.
8. What staff training should you put in place?
DORA stipulates that all staff, including Board members, must stay current with the necessary knowledge and skills to understand and assess ICT risk and its potential impact on the entity.
In practical terms, this means that all staff members should develop and maintain an understanding of the following:
- Basic technical and organisational aspects of ICT security and resilience
- The significance of ICT security and resilience to the financial entity
- The specific ICT-related risks facing the financial entity; and
- The measures the financial entity has implemented to mitigate those risks and the associated acceptable risk tolerances.
We recommend that you have:
- Mandatory annual training: Enrol all staff and ensure completion of the mandatory training provided.
- Specific DORA Responsible Officer training: Arrange specific training for the appointed DORA Responsible Officer. This should be organised by the local Board.
- Encourage positive culture of operational resilience: Provide regular internal communications to explain why operational resilience is important to the business and how everyone has a role to play in achieving and maintaining strong operational resilience for the firm.
9. What should your ICT risk tolerance be?
The Board is responsible for setting and approving the digital and operational resilience strategy, which includes determining the appropriate risk tolerance level for ICT risk within the entity.
In advance of the DORA implementation date, you should:
- ICT risk register and assessments: Maintain a comprehensive ICT risk register and conduct regular risk assessments that are aligned with the risk appetite statement. Ensure that this statement is updated and reviewed at least annually to reflect current risk tolerances and organisational priorities.
- Inventory of IT assets: Develop and maintain an inventory of all IT assets, classified by their business criticality. Map these assets to critical or important business services to understand their impact on operations. This inventory should be regularly updated to reflect changes in the IT environment.
- Business impact analysis: Prepare a Business Impact Analysis (BIA) to assess the business criticality of IT assets to business services. The BIA should be refreshed at least annually or whenever new services are introduced. Have contingency plans in place to address disruptions to critical assets, including the use of alternative providers.
10. Do you need to report ICT incidents to the regulator?
One of the more manageable aspects of complying with the DORA is ensuring that roles and responsibilities are clearly assigned within a documented incident response plan. You may well already have this, but DORA introduces a new requirement: the mandatory formal reporting of incidents to local regulators, which was previously optional.
Luxembourg is the first jurisdiction where this requirement has been implemented, with specific timelines for reporting. The initial notification must be made within 4 hours after the classification of the incident as major, and not later than 24 hours from the incident first being detected. Following this, there is a second window of 3 working days to provide further details about the incident, including what went wrong, the status, and the recovery actions being taken. Finally, a third submission is required, within 20 working days, to close out the incident, detailing the root cause and the current state of operations.
This requirement to report both operational resilience and cybersecurity incidents directly to regulators is becoming more common, and has already been in place for the payments and e-money sector for several years. You therefore need to have plans in place, understand the reporting timelines, and integrate these into your incident response planning. The clock starts ticking from the moment an incident is detected, making timely reporting crucial.
It is important to note that not every incident needs to be reported; only those classified as major ICT incidents, as defined by a written standard. Additionally, there are scenarios where clients need to be informed about the incident as well.
In the event of an ICT incident, you are also required to undertake a comprehensive post-incident review, which will include a detailed 'lessons learned' exercise to inform the updating of your ICT risk management framework.
11. How should I approach managing third party service providers?
In the financial services industry ICT third-party service providers play a crucial role. However, relying on these external entities without proper oversight can lead to significant risks. This is where the Digital Operations Resilience Act (DORA) comes into play, emphasising the need for organisations to conduct thorough analysis and ensure their third-party providers are meeting their obligations.
We recommend:
- Appoint responsible parties: Designate individuals or teams to oversee third-party relationships.
- Conduct thorough analysis: Evaluate the provider's security measures, data handling practices, and compliance with relevant regulations.
- Monitor performance: Regularly assess the provider's adherence to agreed-upon terms and service level agreements.
- Clear contractual terms: Ensure contracts with third-party providers clearly outline their responsibilities and obligations.
- DORA-compliant clauses: Include specific clauses that address data protection requirements.
- Regular reviews: Periodically review and update contracts to reflect changes in regulations or business needs.
It is also vital that you consider the entire supply chain and who your third-party providers are dependent upon. As the recent CrowdStrike incident has highlighted, it is crucial that you maintain sufficient oversight of increasingly complex ICT supply chains that involve third, fourth, or even fifth-party providers.
Conclusion
DORA compliance is achievable for financial entities through a pragmatic approach. By focusing on existing governance structures, leveraging GDPR efforts, and identifying targeted gaps, firms can ensure compliance without a complete overhaul of their current practices.
Ocorian, in conjunction with our colleagues at Bovill Newgate, has developed a new service to assist our clients and other institutions with achieving DORA compliance.


